How-To
How to Remove Internet Trace and Why Do It – Definitive Guide

Every time you surf the internet on any page you access, a fingerprint or path is created that can be easily traced either by companies that are in charge of analyzing BIG DATA or by dangerous hackers who can steal our data. information for harmful purposes, so can the fingerprint be erased?
What is digital trace and how to remove IP trace?
When we talk about a trace or fingerprint, we refer to any action we carry out on the network using personal data. It can be something as simple as entering our email on a platform, searching with our user in an unsafe browser, etc. Sometimes we leave a digital trail on purpose, because we make a record, but other times we don’t.
Some pages and applications make data such as our IP, history and others for commercial purposes, but in these ways they violate our privacy exposing us to hackers, who already know where to find our information. For this we must take security measures, protecting our data.
The most basic measure we can take is to eliminate the IP trace. While we cannot undo the history we already have previously on a website, we can start over with a new IP, which is precisely what we achieve when using a virtual private network, or VPN for its acronym in English. There are thousands on the internet, changing our IP to protect us from any tracking. Some are:
- PROTONVPN
- HIDE.ME
- WINDSCRIBE
How to know if my fingerprint has been deleted from the internet
If you have already tried to erase your fingerprint and want to verify it, there are some steps and actions that you must take to be 100% sure. Some of the ones we can follow are:
Verify that your name does not appear in the results
When searching for our name in any search engine, our users and social network profiles will normally appear, in some cases email addresses and labels on the internet. But if we look for our name and other people appear, we can be calmer, since we are out of reach of internet search engines.
Delete all posts you have made
In these advanced times of the internet, everyone has ever made a post on a social network or website. But if we want to remove our entire fingerprint, you need to remove all these posts. It will not be a big problem, because many social networks and platforms allow us to delete them without much protocol.
How to erase your personal data from the internet in a few steps
If at this point we want to delete our data from the network, we will show you the mandatory steps to follow to achieve it. It can be tedious, but in less than a week, we could eliminate our digital trail quickly and easily.
Delete accounts on social networks and other platforms
Despite using our information to sell products and advertising, any internet service that has our data must allow us to remove it from their site. This applies to social networks, platforms, emails, etc. Even in some of these we can download all our data, so we do not lose all of our past user.
Use anonymous or private accounts
Given the case that we want to erase our fingerprint, but we do not want to disappear for our friends on social networks, there is a way with which we can reduce the trace we leave, this being to use a private account. Once again, all social networks have a private account option, so with this, we are not 100 percent protected, but more than using public accounts.
Using disposable phones
Use secure and private browsers
Stop using Google as a search engine
Use VPN
Use secure instant messaging apps
Is it really possible to minimize your fingerprint?
Delete a fingerprint
The big question in this situation is: Can you erase a fingerprint and the traces that we have left? And the simple answer is that it is very difficult to do it completely, much more if you have been accessing the internet for years and sharing your personal information, however it is possible to reduce these digital marks.
Knowing that you cannot disappear from the web just by pressing a button that says delete, you must begin to reduce the digital trace by erasing information little by little, it should be noted that this is a somewhat slow process and that it cannot be done overnight.
It is important to know that if you want to keep your personal information on the web to a minimum, you must leave social networks so you must be very sure of doing this process.
Social networks such as Facebook, Instagram, or Twitter have the delete account button, therefore it is very easy to unsubscribe from these applications, in the same way, this process must be done in virtual stores such as Amazon or eBay.

In this sense; Emails must also be deleted, used or unused, as well as accounts that are linked to said emails, this process seems complicated because we may not remember where to register but this has a solution.
Digital Trace
All people have left a trace on the web that even they themselves do not know they have done since thousands of blogs are created daily or log-in records are made on any page or social network.
The data provided are traceable by anyone with advanced computer skills or by the companies that are responsible for carrying out these actions, many times illegal for data analysis.
When accessing the internet, it is known that you cannot have complete privacy or anonymity since you always leave some trace or trace; These are defined as any action left by individuals, whether natural or legal.
The disclosure of data by people can be explicit when sharing photos on different social networks or reveal their date of birth, city of origin, telephone numbers, and even bank accounts in the records of pages or emails.
However, we also implicitly share information, without knowing it when entering any page, where its creator can know data from our computer such as the browser we use, the IP address, and even the operating system of our computer, as well as the last website visited. before entering that page.
Applications to erase the digital trail
There are times when we cannot eliminate certain data so it is necessary to send a letter to Google asking to eliminate some information.There are also applications that allow us to erase the traces that we have planted deep in the web, some more precise than others as well as there are private and free.

One of the most frequently used applications for this arduous process is: Delete me, which is a private application that currently costs approximately $ 11 per month.
Delete me specializes in eliminating us from the databases of American companies and even around the world, it is also in charge of deleting all the data that appears about us in Google.
On the other hand, within the free applications, desires are widely used, which are extremely effective in eliminating records made with the mail in different spaces.
This application scans the mail and shows all the records on pages made with said mail and gives the option to delete the records or subscriptions.
How-To
How to Fix Blurred Images/Photos on Android Phones

Why your photos can be blurry (blurred) There are several factors that cause them, including: When taking photos it is unstable (shaky), the object you are photographing is a moving object, the camera lens is dirty, the camera application is not functioning properly and several other causes.
How to Fix Blurry Pictures Taken from Android Phone:
1. Use an app to fix blurry photos
Most image editing apps include a useful function to sharpen photos, this feature you can use to improve your Android photos.
As for the method, I have discussed it in a previous article here
Or you can also try other apps like VanceAI and Neural. love, Let’s Enhance, and MyEdit
2. Take precautions so that the photos are not blurry
Tips for preventing blurry images on Android phones, there are several things you can try to prevent this, including:
- Clean your phone lens
- Take photos in better lighting conditions
- Delete the Camera application cache, go to the menu: Settings > Storage > Devices > Cached data > Clear cached data > OK.
- As much as possible, avoid excessive zoom functions when taking photos on an Android cellphone camera.
How-To
How to Fix Spotify AI DJ Not Showing

As a music streaming service, Spotify has revolutionized the way we listen to music. One of its most exciting features is the AI DJ, which creates custom playlists based on your music preferences. However, sometimes users encounter an issue where the AI DJ feature is not showing up. In this article, we will go through a step-by-step guide on how to fix this issue.
Step 1: Check for Updates
The first thing you should do is check if your Spotify app is updated. If not, update it to the latest version. This may resolve any glitches or bugs that are causing the AI DJ feature to disappear.
Step 2: Clear Cache
Clearing the cache on your Spotify app may also help resolve this issue. To do this, go to your app settings and select “Storage.” From there, tap on “Clear Cache” and restart your app.
Step 3: Disable Battery Saver
Sometimes, battery saver settings can interfere with the app’s performance. To disable the battery saver, go to your phone’s settings and select “Battery.” From there, disable any battery-saving modes that are enabled.
Step 4: Check the Internet Connection
Make sure that you have a stable internet connection. If your internet connection is slow or unstable, the app may not be able to load the AI DJ feature.
Step 5: Check Country Settings
Spotify’s AI DJ feature is not available in all countries. If you’re using the app in a country where this feature is not available, it may not appear on your app. You can check the list of countries where the AI DJ feature is available on the Spotify website.
Step 6: Check the Subscription
The AI DJ feature is only available to Spotify Premium subscribers. If you’re using the free version of the app, you may not be able to access this feature.
Step 7: Reinstall the App
If none of the above steps work, you can try uninstalling and reinstalling the app. This will reset the app to its default settings, which may resolve any issues that were causing the AI DJ feature to disappear.
Step 8: Restart Your Device
If the issue persists, try restarting your device. This can help fix any software issues that may be causing the problem. Here’s how to do it:
- Press and hold the power button on your device.
- Tap on the “Restart” option when it appears on the screen.
- Wait for your device to restart, and then try opening the Spotify app again.
Step 9: Contact Spotify Support
If the issue persists after trying all the above steps, it’s time to contact Spotify support. You can reach out to them through their website, and they will guide you through resolving the issue.
Conclusion
Spotify’s AI DJ feature is a great way to discover new music based on your preferences. However, it can be frustrating if it’s not showing up on your app. By following the steps outlined above, you should be able to resolve the issue and get back to enjoying your music. Remember to check for updates, clear cache, disable battery saver, check internet connection, country settings, and subscription, and reinstall the app. If all else fails, don’t hesitate to contact Spotify support.
How-To
How to Overcome steam error code e84
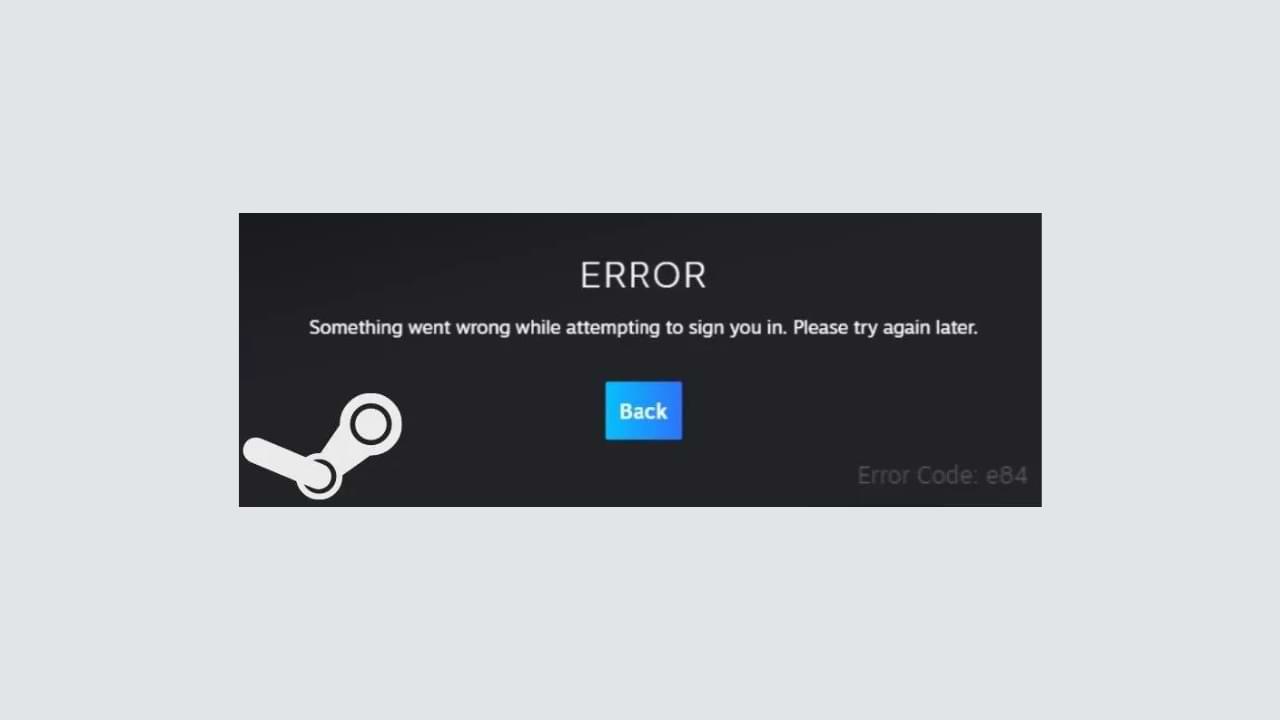
The steam error code e84 problem usually occurs when we are about to log into the Steam platform, this error is also accompanied by Something that went wrong while attempting to sign you in.
If you are currently experiencing the same error. So in this article, we are going to provide you with the repair solution with the simplest way to fix it.
1. Delete Temporary Files
Temporary Files on your computer can sometimes make Steam run improperly. One is the steam error code e84, so try deleting temporary files from your computer. To do so, follow these steps:
- Press the Windows key + R then type the command %temp% and press the Enter / OK key
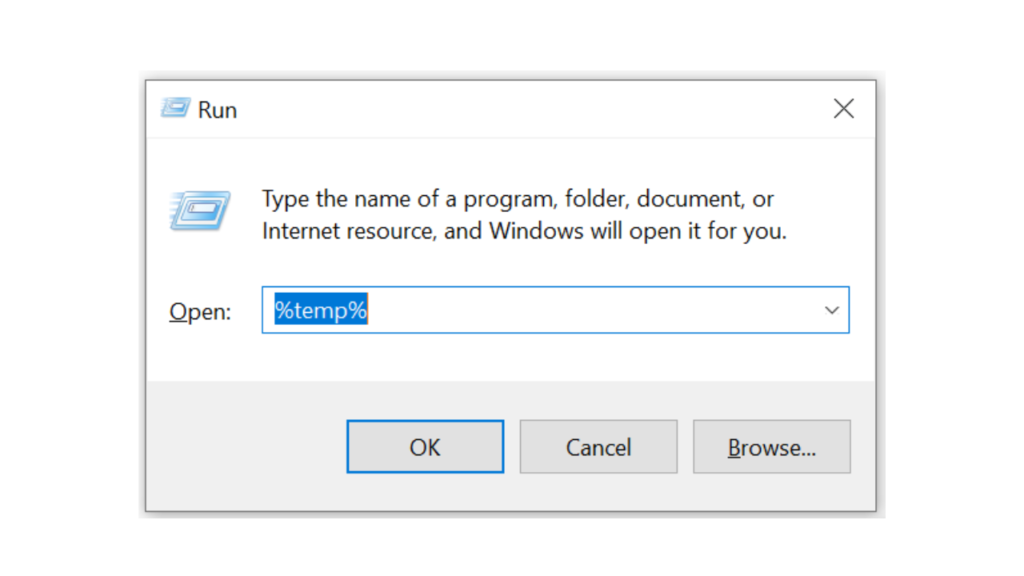
- Then delete all files and folders in the temp folder
- After that, try restarting your computer, and try opening Steam, is the error code E84 still there?
Deleting all of these folders will not cause errors or damage to the computer/programs on your computer, because all the files in this temp folder are temporary files that are no longer needed.
2. Update the Steam Application
Check if there is an update available for the steam application, if there is, please update immediately. And after the update is complete, try opening the Steam application again.
3. Reinstall the Steam App
If the two methods above don’t work, there could be some problematic or damaged Steam system files. The best solution is to reinstall the Steam application.
-

 Phones5 years ago
Phones5 years agoApple iPhone 11 (2019) – Release, Info, Leaks, Rumors
-
![Huawei's New Operating System is HarmonyOS [ Officially ],harmony os,huawei new operating system, huawei harmony OS,](https://www.thedigitnews.com/wp-content/uploads/2019/08/Screenshot__2285_-removebg-preview-2-1-400x240.png)
![Huawei's New Operating System is HarmonyOS [ Officially ],harmony os,huawei new operating system, huawei harmony OS,](https://www.thedigitnews.com/wp-content/uploads/2019/08/Screenshot__2285_-removebg-preview-2-1-80x80.png) Phones5 years ago
Phones5 years agoHuawei New Operating System is HarmonyOS [ Officially ]
-

 News5 years ago
News5 years agoBelle Delphine bath water – Instagram Model Sells Used Bathwater For 30$ To Their Loyal Followers
-

 Tech5 years ago
Tech5 years agoLevi’s Bluetooth Jacket Lets You Control Your Smartphone