News
Gmail Gets New Look Soon, Similar To Outlook

In terms of User Interface, in the last few years, Gmail has only received minor updates, but regarding this, it seems that it will soon change because some time ago Google announced that they had prepared a new user interface for users to use.

Now as you can see above, that is how Gmail looks now, and will soon be replaced with the following user interface:
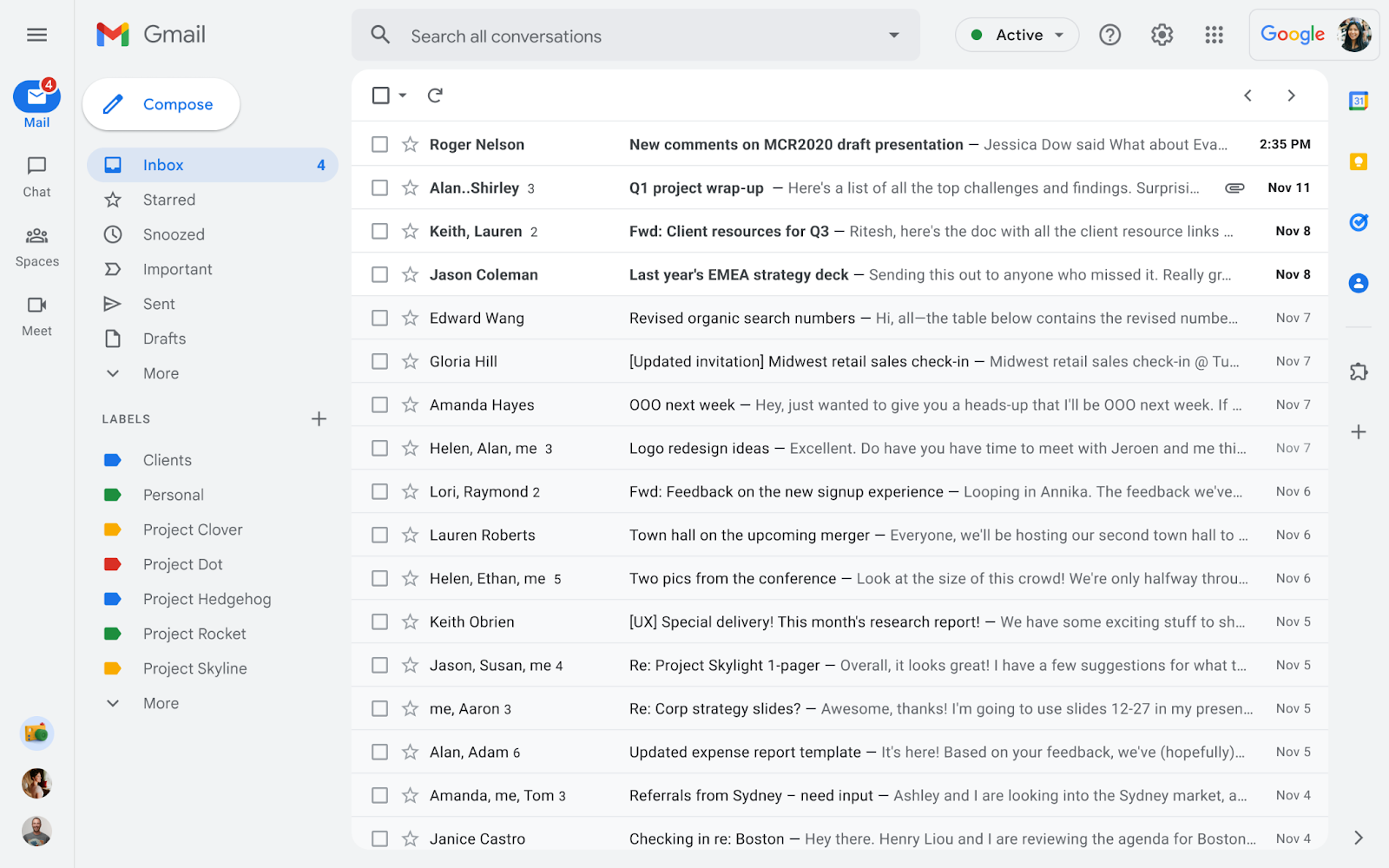
Now at first glance, Gmail’s new user interface is similar to Outlook, where on the side you can switch to Mail, Chat, Meet and Spaces, and some layouts that I see are quite similar to Outlook.
Although it looks similar, of course, this is not a problem, considering that Google itself describes that this user interface is made so that users can easily switch to other Google applications/services, including Meet and others.
Regarding this new user interface, Google noted that all Gmail users will get this new look, except Workspace Essentials and Admin can’t change the appearance again after getting this update, in other words, later before everything goes perfectly, Google will provide a small banner that invites users to switch to a new view, and reportedly this will start on February 8th and end at the end of Q2 2022.
Via: Google
News
iOS 16.6 close. What’s new with the update for iPhones?

iOS 16.6 is a new update for iPhones, which is about to be released. What’s new in this software update, and what other new operating system versions will Apple release? Let’s see what you should know about the iOS 16.6 update a few days before its planned public availability.
iOS 16.6 is another, slightly larger software update for iPhones that Apple will make available in the days to come. This will happen next week. Let’s see what’s new in this update and how to prepare the phone before its public launch for everyone.
From Beta to RC
Apple released the first beta version of iOS 16.6 in the second half of May. Even before this year’s WWDC 2023 conference. A few days ago, the RC release was released to developers and testers, which is basically close to the final update. The same build should be made available to all iPhone users.
What’s new in iOS 16.6
The official changelog for the iOS 16.6 update is very sparing of words. Apple has introduced here basically only fixes for various bugs, including those related to security. So the update does not bring any major news. The official changelog is below.
This update contains important fixes, including security fixes, and is recommended for all users.
Information about the security content of Apple updates can be found on this page.
However, the iOS 16.6 update contains some information related to the introduction of HomePod speakers in other markets. This time it will be Israel because the software has added support for the Hebrew language in Siri. Apple does not have its own showrooms in this country, so sales will probably take place through partner stores.
This is not the only update
Along with iOS 16.6 for iPhones, Apple will also release other updates. These are macOS 13.5, watchOS 9.6 and tvOS, iPadOS, and new software for HomePods with numbers 16.6. Let’s expect all of these updates to be in the hands of users of compatible devices as soon as early next week, possibly on Monday. This will take place around 19:00 our time.
Software installation will be possible after going to the Settings, General, and Updates sections on iPhones. Here, after a while, information about the availability of iOS 16.6 will appear, which should then be downloaded. It will be possible to install the update when the phone battery is charged to at least 50%. or 20 percent, but then the device must be connected to the charger. Of course, you should make a backup first. It’s just in case something goes wrong.
We will have to wait for the news until September when Apple will make iOS 17 and other new systems presented in June available. They are currently in a pilot program and can be tested in preview betas.
News
Huawei Announces Plans for Commercial 5.5G Network Device Launch in 2024
The leading provider of information and communication technology (ICT) solutions, Huawei, announced plans to launch a full range of commercial 5.5G network devices in 2024. The launch will mark the 5.5G era in the ICT industry, which is built on end-to-end solutions by integrating advanced and comprehensive technologies.
The announcement was made by Yang Chaobin, Director and President of Huawei’s ICT Products & Solutions, in the midst of holding the 5G Advanced Forum. This is a forum that is part of the Mobile World Congress (MWC) Shanghai 2023 event.
Over the past four years, the implementation of 5G technology has increased rapidly and has started to yield tangible financial benefits. There are currently more than 260 commercial 5G networks worldwide, serving more than 1.2 billion users, and there are already 115 million gigabit F5G users. As service and content models continue to evolve, breakthroughs in technology, such as glasses-free 3D viewing, are creating unprecedented immersive experiences for users.
However, to be able to deliver such cutting-edge services, higher 5G network capabilities are needed. In general, industry players agree that 5.5G will be a milestone in the evolution of 5G , and the technology is getting closer to both users and enablers.
Huawei proposed the “ 5.5G Era ” concept, built on an end-to-end solution that integrates comprehensive and advanced technologies, including 5.5G , F5. 5G , and Net5. 5G . With this solution, the investment that operators have made for the 5G network will remain safe, and at the same time they will experience an increase in network performance of up to 10 times.
The 5.5G Era will deliver peak downlink speeds of 10 gigabits and peak uplink speeds of gigabits to meet increasingly diverse service needs. This solution will also redefine the vision of the industry through the use of new technologies such as passive IoT to open up the market with 100 billion IoT connections.
“With the standardization schedule set, the 5.5G Era is ready to enter the technology and commercial verification stage. In 2024, Huawei will launch a full range of commercial 5.5G network devices in preparation for the commercial deployment of 5.5G networks. We look forward to working together with all industry players to start a new journey toward the 5. 5G era, “said Yang.
In order to drive the implementation of end-to-end 5.5G solutions, Huawei has been working closely with players across the industry for the R&D process as well as the verification of key 5.5G technologies. In this verification process, Huawei has made significant progress, especially for extremely large antenna arrays (ELAA) that enable 10-gigabit downlink speeds, flexible spectrum access that helps achieve uplink speeds in gigabit units, and passive IoT. which can enable 100 billion IoT connections.
The other key technology involved is 50G PON, which can deliver 10-gigabit speeds for the F5’s ultra-broadband network. 5G, which in the future is expected to be widely used in homes, campuses, as well as production facilities. Huawei has cooperated with more than 30 operators around the world in the framework of technology verification and application trials for this technology.
In addition to information on key technology development for 5.5G wireless and optical access networks, Yang Chaobin also said that Huawei has been working on applying AI native technologies to the core 5.5G network, to continuously improve network capabilities and availability. In this way, AI (artificial intelligence) capabilities will be able to be passed to the end of the network to better serve more industries.
Net5. 5G promises 10-gigabit access, ultra-broadband transport, and microsecond-level latency on AI networks, so it can serve as the foundation for the next generation of networks for industrial digitization processes by providing high-quality network access.
The industry is currently in the early stages of developing a vision for 6G, and has just started research on the key technologies that will become the pillars of 6G. It’s no wonder that many industry players are turning to 5.5G as their milestone for future development. The 10-fold increase in network capabilities provided by Era 5. 5G will enable digital technology productivity to be achieved in various industrial sectors.
MWC Shanghai 2023 takes place from June 28 to June 30 in Shanghai, China. Huawei will showcase its products and solutions at booths E10 and E50 in Hall N1 of the Shanghai New International Expo Center (SNIEC). Together with global operators, industry professionals, and opinion leaders, Huawei will explore topics such as accelerating the realization of prosperity with 5G, moving towards the 5.5G era, and intelligent digital transformation.
The arrival of 5.5G is driving the creation of new business values in areas such as connecting people, the Internet of Things (IoT), and the Internet of Vehicles (IoV), as well as supporting many industrial sectors on their transformation journey towards a smart world.
News
Samsung, the arrival of the Galaxy S23 FE is increasingly probable: the battery is certified

The “Fan Edition” of the Galaxy S range would be ready to return to the market after a year’s break, probably due to the lack of processors that had put the entire technology sector in serious difficulty.
CERTIFIED THE BATTERY
South Korean certification site Safety Korea recently tested the battery of what could be Samsung’s new Galaxy S23 FE. The battery in question, made by Ningde Amperex Technology Limited, is identified with the initials EB-BS711ABY. The smartphone, however, has the initials SM-S711.

A photo of the battery is also included in the certification document, an image that is not particularly defined which unfortunately makes it extremely difficult to detect other details as well. The capacity is likely to be 4500mAh, in line with previous rumors. Present, however, the now classic blue sticker that allows for faster removal in case of replacement.
According to rumors that have been increasingly intensifying over the last few weeks, after those of recent months which were more suspicious about the possible creation of a new Galaxy “Fan Edition”, the Galaxy S23 FE should share most of its hardware features with the current Galaxy S23. At the moment, however, information is still rather scarce.
POSSIBLE LAUNCH TOWARDS THE END OF THE YEAR
Usually, the “formula” of the Galaxy S FE is to bring the characteristics of the higher-end versions into a more accessible device from an economic point of view which, on the one hand, could allow the purchase to a wider public, on the other to Samsung to increase sales, down after a decidedly good and encouraging start.
According to analysts, in fact, during the second quarter of the year, Samsung could record a decline in sales of about 20% compared to the same period last year.
Further rumors would also point to the use of an Exynos 2200 processor instead of Qualcomm’s Snapdragon, which could also benefit its semiconductor division.
On the camera side, however, the Galaxy S23 FE could integrate the same main sensor as the Galaxy S23, a 50-megapixel sensor that could represent a significant improvement over the previous FE versions of the Galaxy S range.
Finally, as regards the launch, it could take place towards the end of the year, certainly after the launch of the new Z Flip and Z Fold expected for the end of July.
-

 Phones5 years ago
Phones5 years agoApple iPhone 11 (2019) – Release, Info, Leaks, Rumors
-
![Huawei's New Operating System is HarmonyOS [ Officially ],harmony os,huawei new operating system, huawei harmony OS,](https://www.thedigitnews.com/wp-content/uploads/2019/08/Screenshot__2285_-removebg-preview-2-1-400x240.png)
![Huawei's New Operating System is HarmonyOS [ Officially ],harmony os,huawei new operating system, huawei harmony OS,](https://www.thedigitnews.com/wp-content/uploads/2019/08/Screenshot__2285_-removebg-preview-2-1-80x80.png) Phones5 years ago
Phones5 years agoHuawei New Operating System is HarmonyOS [ Officially ]
-

 News5 years ago
News5 years agoBelle Delphine bath water – Instagram Model Sells Used Bathwater For 30$ To Their Loyal Followers
-

 Tech5 years ago
Tech5 years agoLevi’s Bluetooth Jacket Lets You Control Your Smartphone